发现加密请求js脚本
对浏览器前端进行审计,发现了加密的js
1 | |
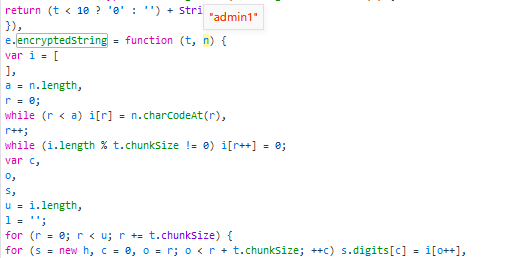
打下断点查看变量,发现了明文和密文变量名
找到js内发送请求处
1 | |
打下断点查看变量
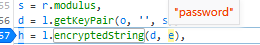
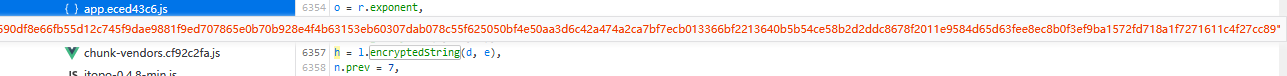
发现在js里面就是在这里生成密文并发送到服务器端
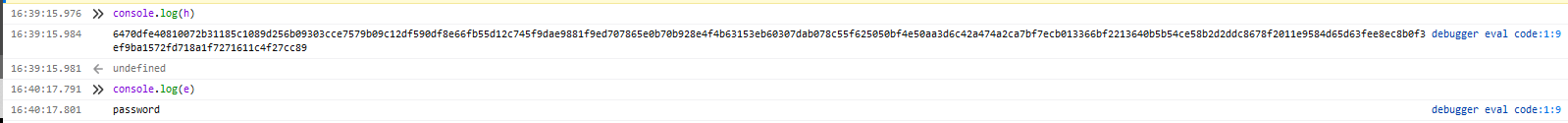
调用js生成加密密码字典
在控制台内申明一个明文字典数组
1 | |
声明一个空数组作为密文字典
1 | |
调用加密方法将明文字典加密为密文字典
1 | |
然后在控制台内就获得了加密后的字典文件
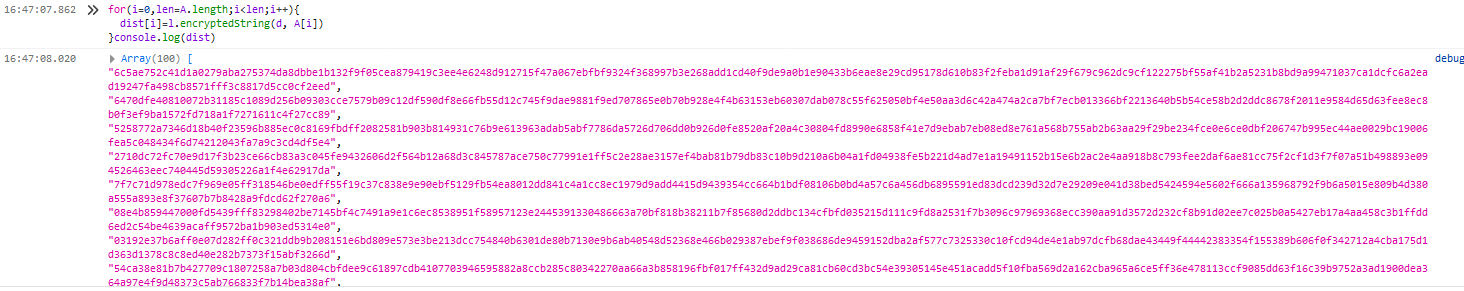
直接使用加密后的字典文件放入burp里面进行爆破就可以了
这套操作也适用于请求加密的情况,可以直接替换掉加密请求达到请求篡改的目的